The blind spot in Zero Trust
A Zero Trust architecture assumes attackers are always present, and trusted relationships must be explicitly declared and lifecycled for every enterprise resource. The approach is to never trust, always verify.
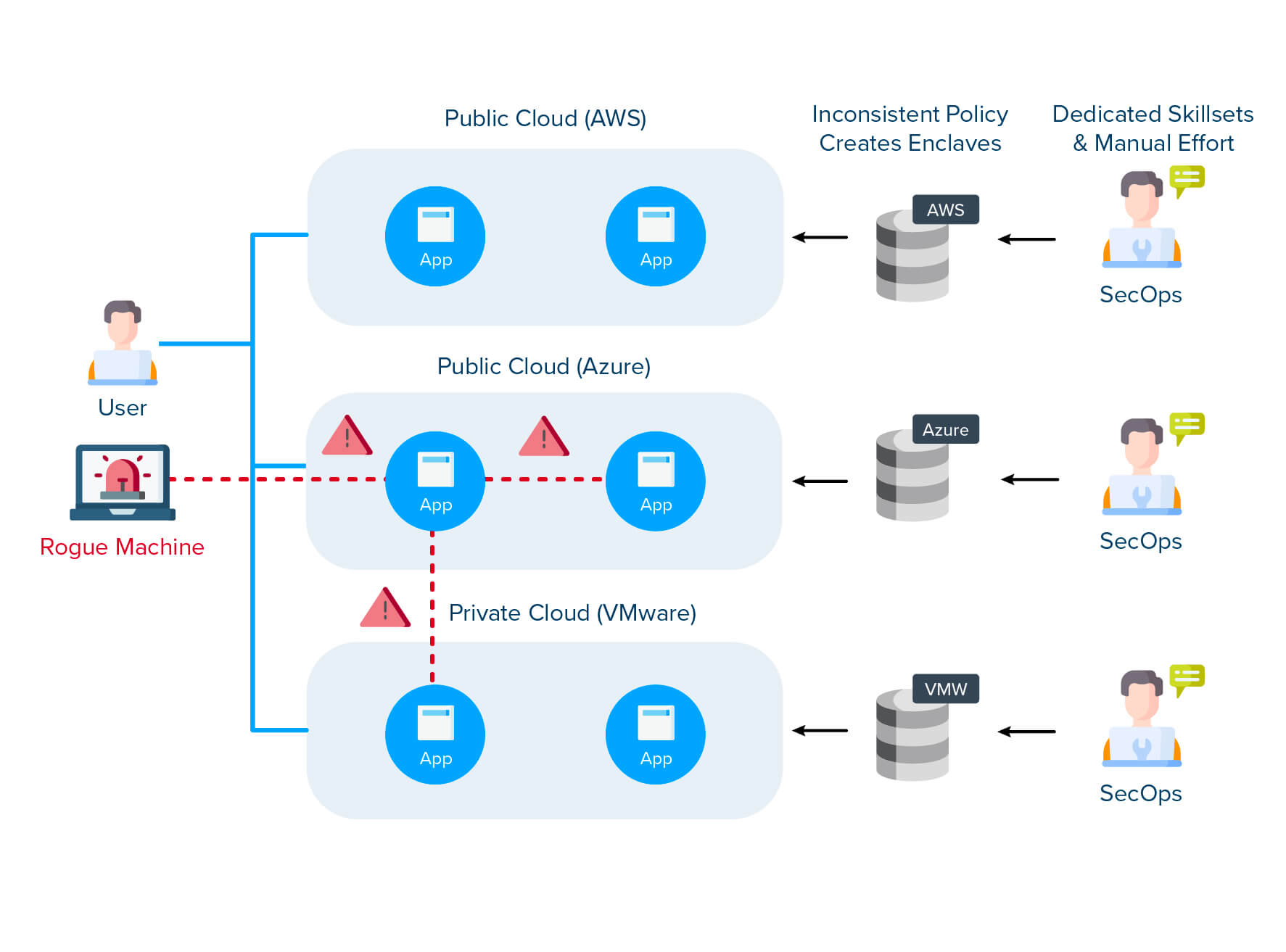
Poor visibility inside the enterprise perimeter can trip up your Zero Trust policy enforcement. Without a complete view of the relationships between applications, users, devices, machines, and workloads, the result would be incomplete protection and security gaps.
Moving from a vertical and siloed perspective to an application-centric view across multiple applications and services is essential and helps overcome security visibility challenges, which is the foundation to create an effective Zero Trust Architecture.

Orchestrated segmentation: a foundational step for Zero Trust
To adopt Zero Trust, enterprises should leverage a key enabling approach—microsegmentation–so that the correct security policies can be applied to the correct workloads and services. By placing security controls next to the workloads themselves, security policies become asset-specific. As a result, workloads at different security levels can now share a common security framework for greater protection and agility.
Analysts recommend enterprises begin Zero Trust implementation projects with segmentation: isolating workload-to-workload and application-to-application communications based on Zero Trust security policies. This requires enterprise-wide visibility first to succeed.
Learn more
Get Zero Trust right from the start
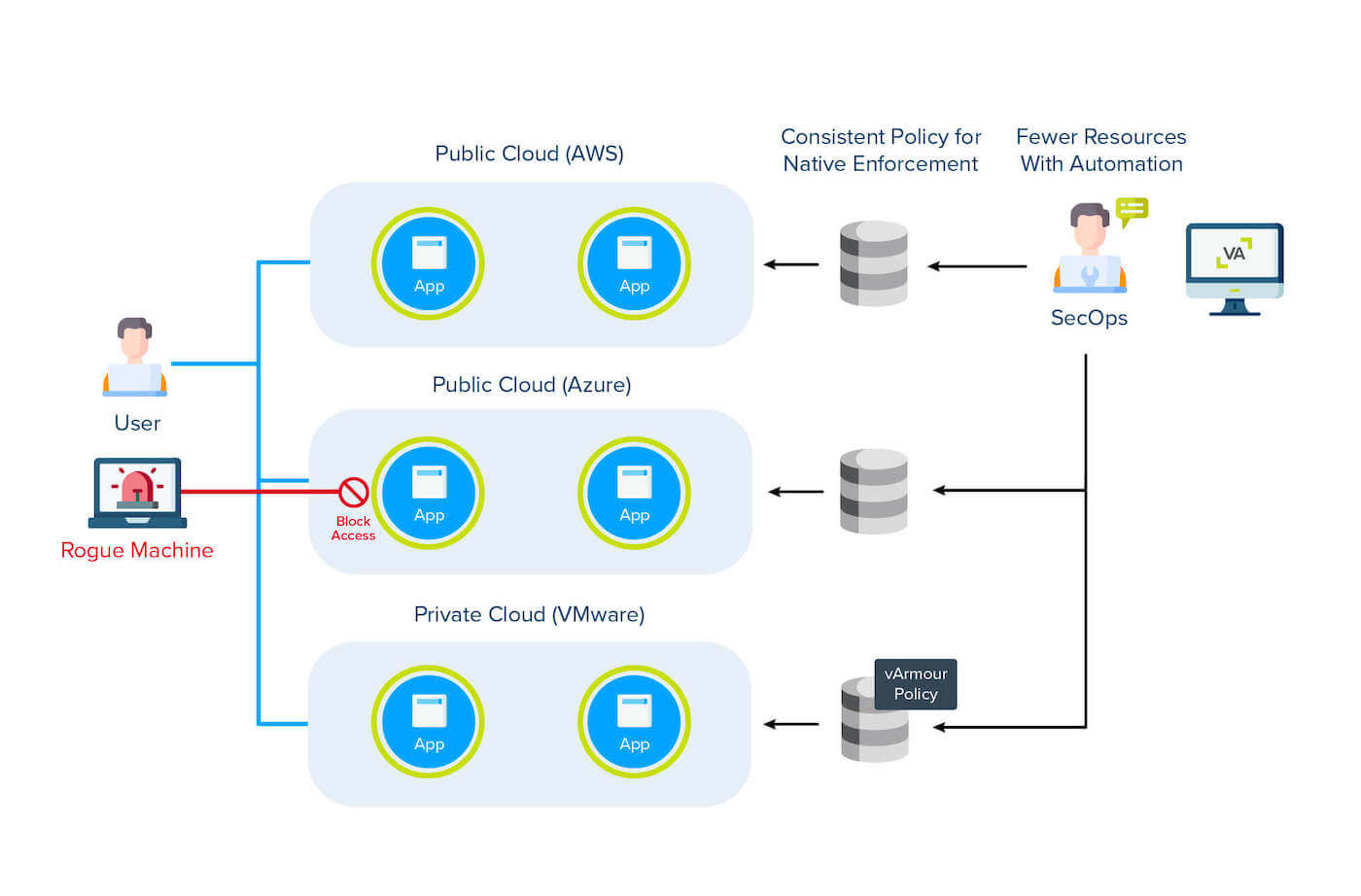
Your journey begins with understanding and visualizing your enterprise environment, because you can’t protect what you can’t see. With vArmour, you can map the constantly changing relationships and dependencies between applications, data, devices and users. With this baseline, you can determine the policies, and enforce them across networks, infrastructures, and clouds within the Zero Trust framework.
With no new agents to deploy, you are running fast with full coverage across your hybrid cloud. Compute intent-based Zero Trust policies and orchestrate to your existing enforcement platforms to accelerate protection and reduce your risk.
Learn more
Get details on the five steps in a Zero Trust journey
Quickly discover and visualize applications and their relationships across an entire IT estate in near real-time.
vArmour Application Dependency & Relationship Mapping Solution Brief
Gain unprecedented visibility and insights into all their applications across every environment.
Application Relationship Management (ARM): An Overview
Visualize and control user relationships from the application-out.
Application Access & Identity Data Sheet
Accelerate your Zero Trust journey with vArmour application visibility and security solutions.
Five Reasons Why Zero Trust Projects (That Failed Before) Will Succeed Today
Orchestrate Zero Trust policies to native enforcement platforms via APIs.
vArmour Orchestrated Segmentation Solution Brief