Cloud Security: Do you know how big your blast radius is?

If you don’t know how big your blast radius is, that’s just a ticking time bomb… waiting to go off.
Cloud transforms your blast radius of an attack exponentially and it is imperative that you understand and respond appropriately to this massive increase of risk. If you can’t answer most of these key questions around cloud security, you are at severe risk:
- Vulnerability Reduction – Do you know exactly what applications and workloads are at risk? How critical are those assets? Where are they located?
- Monitoring & Detection – Can you determine when you are being attacked? Do you know where that attack is happening?
- Incident Response – How can you remediate incidents faster? Can you determine the extent of the blast radius?
- Compliance – How do you know when and how applications are processing and how sensitive data is being processed to ensure continuous compliance?
Let’s take a look at a typical view an AWS admin has of their workloads:
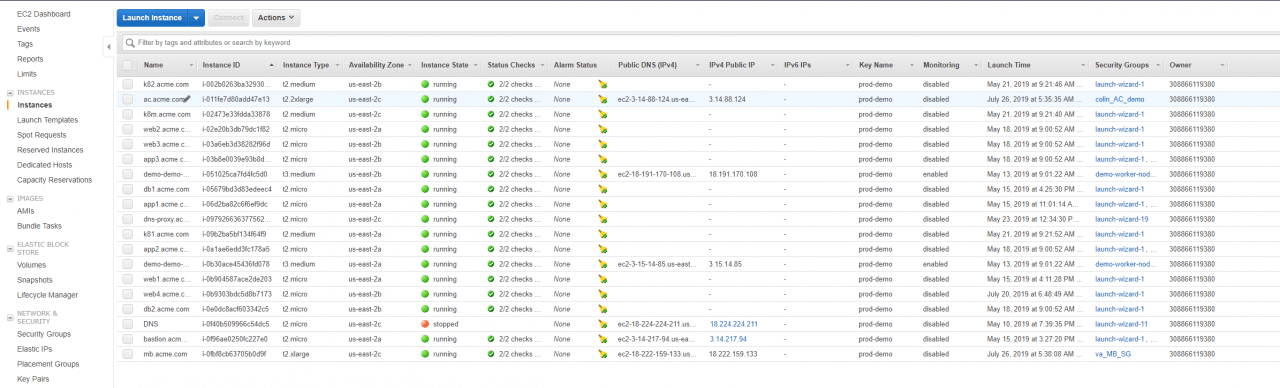
With that limited view, it’s difficult to answer any of the key risk questions we posed above.
Now imagine you have more than 100,000 workloads (common among many enterprises), and each one has 50 to 100 relationships with other workloads. Some quick math will show that’s more than 100 million workload relationships to monitor– resulting in an enormous blast radius. Without a map of these relationships, application boundaries and dependencies are largely unknown, and thus, security leaders can’t understand the blast radius in order to protect from, and respond to, critical threats.
Simply put, you can’t protect what you can’t see.
vArmour provides the comprehensive visibility you need to understand the application dependencies, behaviors and relationships in your blast radius.
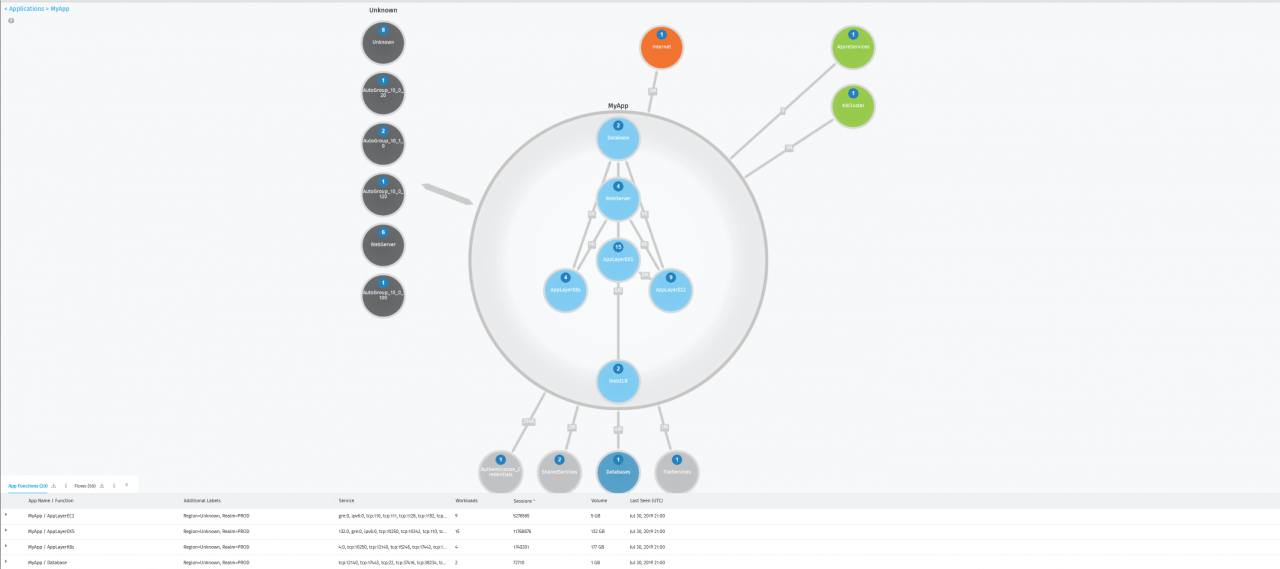
vArmour’s Application Controller builds an enterprise-wide relationship database known as the vArmour Security Relationship Graph. It is a rich source of intelligence and records what workloads and applications are interacting, and the nature of their interactions.
From the comprehensive visibility provided by the graph, you will be able to proactively reduce vulnerabilities, monitor and detect threats, respond to incidents and achieve continuous compliance.
The Security Relationship Graph, coupled with our Cloud Connectors, makes it is easy and quick to integrate any cloud platform such as AWS, Azure, VMware NSX, etc. to easily drive and orchestrate consistent security and compliance policies.
We would love to talk to you about how we can help you with your potential blast radius. Get a 10-Day Free Trial of Application Controller now by contacting us here. It installs in less than 15 minutes. This is a limited time offer and ends 8/13.
To learn more about AWS’s Shared Responsibility Model, take a look here.




