Overcoming Challenges Due to Multi-Cloud IP Address Complexity

Multi-cloud is the reality for most enterprises today. There’s a number of reasons why, including the need to use specific capabilities from different cloud providers, easier migrations for legacy applications such as O365, business or developer preferences due to skill-set or budget, and external drivers like mergers and acquisitions. Plenty of on-premise applications remain in the private cloud as well.
Across these multi-clouds, interdependencies among applications continue to explode, especially among modern applications that have atomized into smaller and smaller microservices. This trend is leading to far greater complexity in the application infrastructure for both individual applications as well as the entire enterprise. This complexity makes ensuring application security and resiliency much harder for operations teams.
One challenge enterprise IT organizations face that you don’t hear much about is managing the internal private IP address spaces across cloud deployments. It’s common to use and reuse IP addresses in different domains, almost like a “vending machine” style model. For example, an enterprise could use 10.123.6.3 in AWS, Azure, and its own private data center as shown in the diagram below. Typically you would think that is just a connectivity problem, something that networking devices like load balancers may need to resolve to provide communications between applications and services.
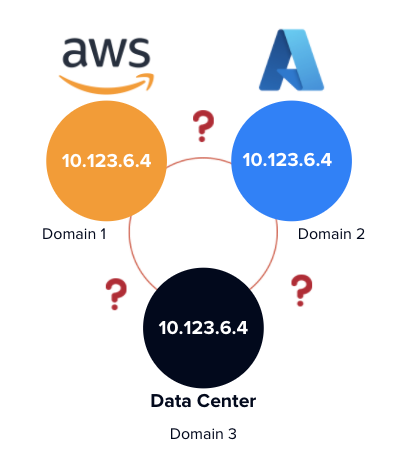
Yet something that seems mundane can also be a significant visibility and security challenge. Because applications cannot be distinguished precisely when using overlapping private IP addresses across multi-cloud, it’s hard to see, understand, and baseline applications and interconnected behaviors. It is difficult to decipher which applications or workloads are requesting access, data, or services from other applications. And if you can’t see it, you can’t define or enforce security policies to protect these applications at any sort of granular level. This is especially true considering many enterprises are now moving away from flat networks protected at the perimeter and applying least-privilege Zero Trust policies to individual applications and workloads.
vArmour provides a common-sense solution to this challenge by appending a unique domain identifier to the IP addresses. This enables enterprises to visualize and control their entire application estate in a single view, without conflicts or confusion, even when IP addresses are repeated or reused across diverse environments.
Operations teams are able to uniquely identify applications and workloads regardless of where they’re hosted and see the interdependencies and data flows between them. From there, organizations can baseline behavior, define, and orchestrate security policies whether detective only, or enforced by each distributed native platform as needed—a significant departure and improvement from a purely networking-based approach, to a more highly-valued posture based on actual business context.
This in turn creates a foundational understanding of what is happening now across an IT estate based on “observed reality,” which is critical to enable operational resiliency during change management or migrations, and to ensure application security moving forward by protecting against unsanctioned access or other policy violations.
The devil is in the details. Addressing overlapping IP address issues for multi-cloud can help enterprises achieve strategic priorities with far fewer resources, workarounds, and mistakes.
Find out more about vArmour’s solutions for managing application relationships across the multi-cloud here.
Follow author Andrew Hendry on Twitter @awhendry




